Phishing is a malicious practice that everyone – companies and individuals – can fall victim to if they are not careful. It is important not to minimize the potential consequences of these practices and to know how to detect and protect oneself from them. This is what we propose to explain in this article.
How to detect a phishing attempt?
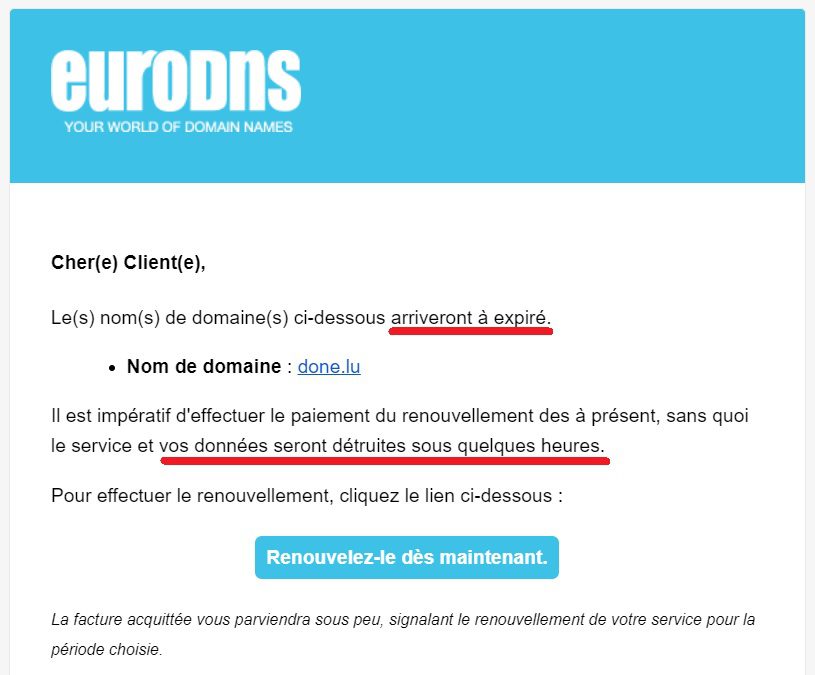
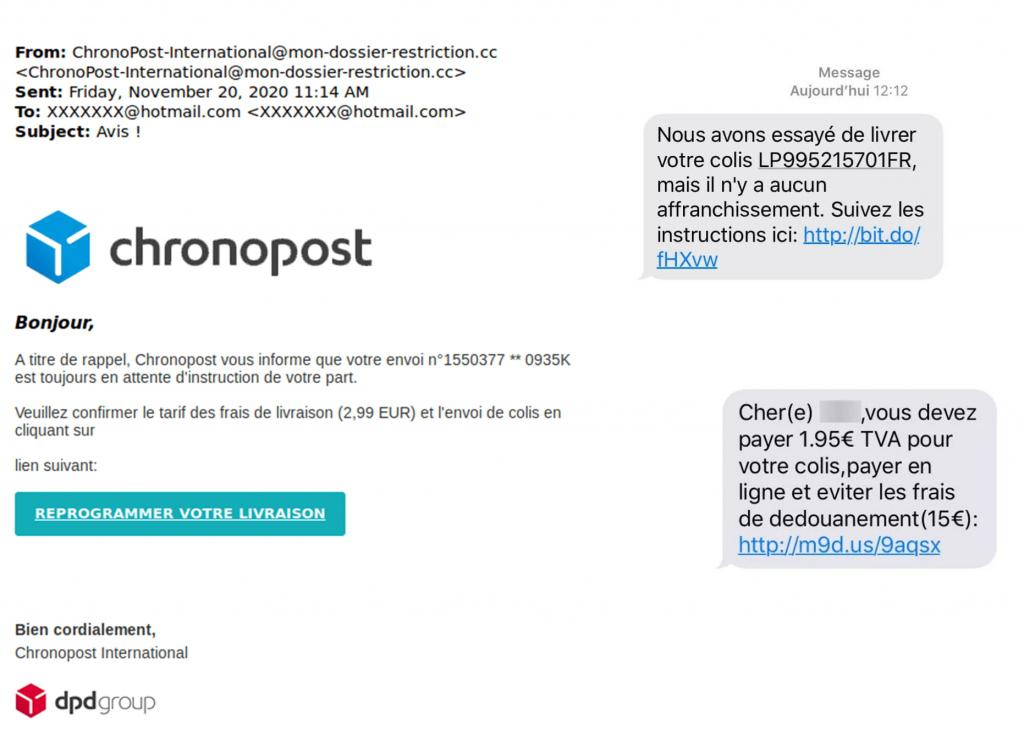
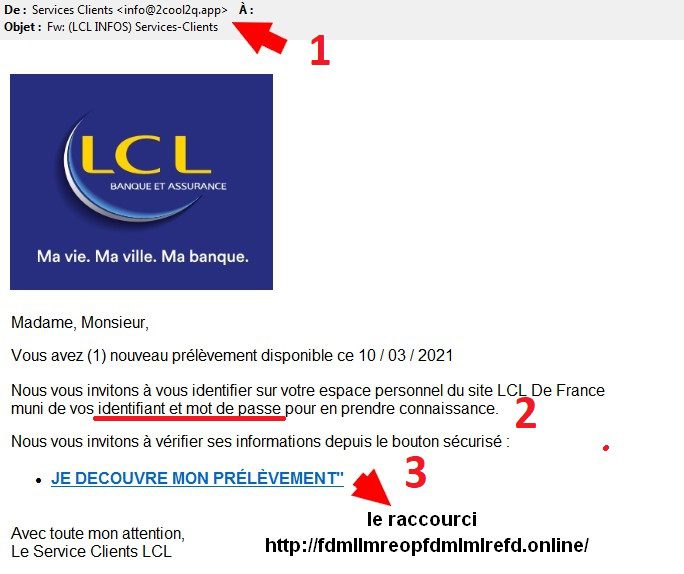
Deceptive phishing is the most common technique. The process consists of copying the visual identity used by well-known companies (banks, telephone operators, delivery services, etc.) in their e-mails, and sending their customers false e-mails whose title and content create a sense of urgency in order to frighten them and persuade them to react quickly to an order.
Let’s take as an example this concrete case that recently happened to our partner EuroDNS (domain name provider and web host located in Luxembourg) and let’s unravel the technique used by the hackers and see how to flush out the scam.
How to react in case of a phishing attempt?
1 – Ask yourself if this e-mail is really intended for you, does it mention a file or an invoice that speaks to you?
2 – Check the spelling and syntax, both in the title and in the content of the e-mail.
3 – Do not click on the link or button that prompts you to take an action (Pay now, Download the attachment, Renew your subscription…)
4 – Check the links in the email. Place the mouse over the link to display the complete link (this manipulation is not possible from a smartphone). Does it point to a legitimate site? Beware of fake domain names that imitate the address of a known website.
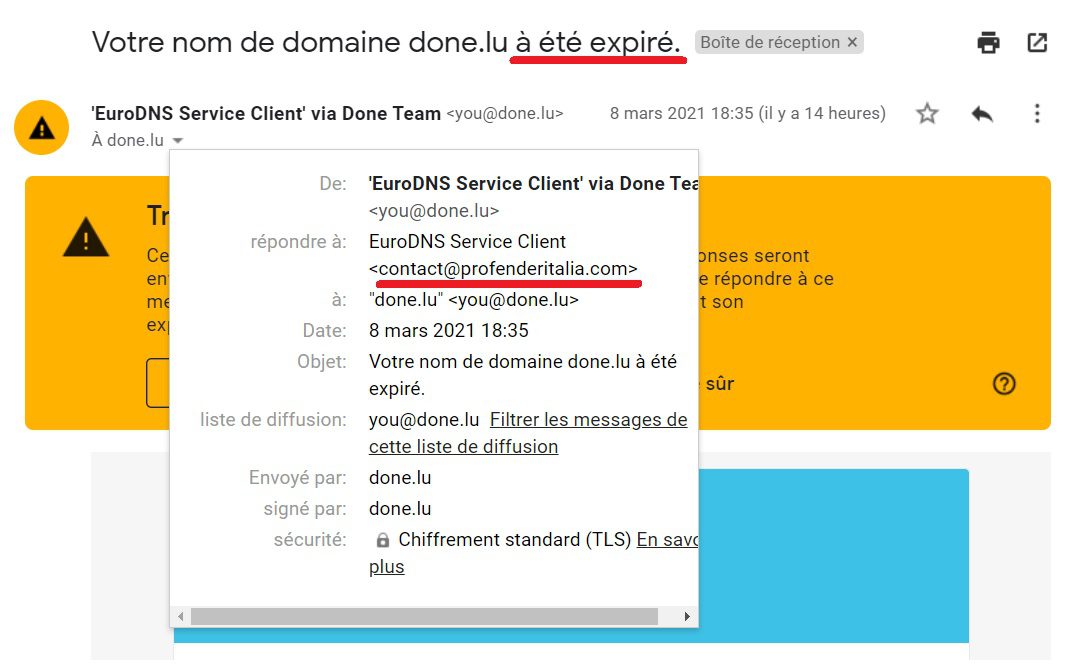
5 – Check the sender’s email. Do it scrupulously because it can sometimes happen that the e-mail address of the sender imitates rather well that of a real company.
6 – Do not open or download any attachments, even if the title of the document seems plausible or inciting.
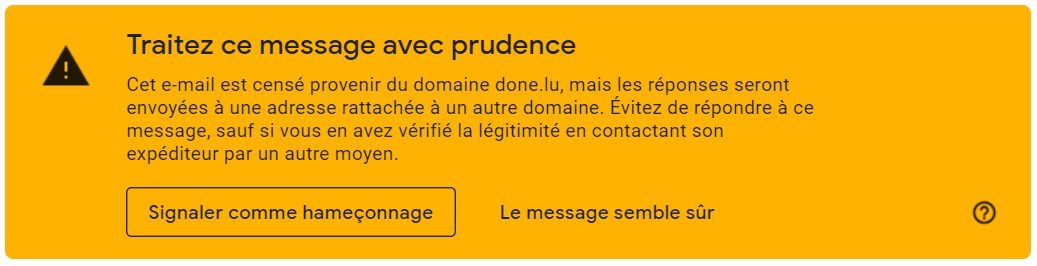
7 – Report it as spam.
8 – Place the e-mail in the trash and delete it. And if you still have any doubts, go directly to the website of the company that the e-mail is trying to abuse – without using the link in the suspicious e-mail, of course – and report the suspicious messages and sites to the companies whose identity has been impersonated.
You can also report these actions to the authorities.
In France: Report fraudulent emails to https://www.signal-spam.fr/ and suspicious SMS to 33700.
In Belgium: Report suspicious emails and SMS to suspect@safeonweb.be
In Luxembourg: the Govcert website informs you about the main past and current phishing attempts: https://www.govcert.lu/
In other countries: The local authorities who are taking care of phishing atempts.
Conclusion.
Always be on your guard!
Wednesday, April 7, 2021